这次比赛Crypto难度比较基础,手速快才是硬道理。
Rank:2
[签到]古典大杂烩
题目描述:
1 | 请尝试解密它。 |
题目:
1 | 🐩👃🐪🐼👅🐯🐩👈👇👭👟👝🐺🐭👉👙👤👋👚🐪🐫👍👢👮👱🐼👢👨👠👭🐽🐰🐻👚👂👧👠👥👛👮👯👮👬🐾👐👛👌👚👞🐨👏👉👆🐿👆👘👇🐺👦🐸👃🐭👟👑👪👃👁🐻🐻👜🐧👇👊🐧🐾🐼👇🐫🐺👐👆👪🐼👋👌👧🐻👐🐩🐺👥🐽👋👉🐰👎👠👠👣🐧🐫👧🐭👢🐯👑👑🐮👂👏🐻👥👚🐮👋👬👌👥👁👣👅👧👯👦👌👌👍👠👌🐽👉👃👊🐫👉🐨🐮👩👆🐪🐯👘👏👏🐼👩👍👊👍👡👀👰👋👣👨👧👍👜👐👛🐮👘👅👠🐿👂👰👄👈👝👠👤👃👛👘🐭👅👱👆👬👫👥👆🐽👁👐👥👊👇👉👊👩👌👭🐫🐫👬👱🐯👇🐺👁👞👑👙🐮👜👋👘👪👩👚👦👨👀👩👐👉👃🐾👥👀🐫👝👍🐩🐧👰👆👇👨🐪👃🐭👦🐫👱 |
第一层很明显是base100,之后的每一层像哪个base用哪个解密即可:
1、 base100:
1 | 2L3EN82QPvhfC6RbmTc34VkwzEkqivF9DcKpindwxwuGYdUcg1XROHOaPCoAL6hZsLJDDe0PS0GEP4CYOsETUpDY2CnFTR9Wiil04p6k8ZZ7KXDnc7TuUnJlNpxoUUViUFRLS4R17rO38aXXErVSVjIyTlqpVeYd7aNiHKyMQfimLda6NzOutnOFJYnSPRSrUv44uz8PCJgZb7eTasrcoqIrYRLGnI4fV20yOPq3L6o4z |
2、 base62:
1 | UlhoYUdxZTdaY1FCbXFyaWl5S0ZKaW4yN2ZiWkpTZHhOd2hBVk1wNzRvUWE0VWs2RXVqTlpkTHNvYVpxNHRMUDd3dXk4OGJiSlhlTGJnN2dxR2RkTm15dGs1S1RGdlk3TmpRR0wzenFrQ3BCM3lmUTFTUkY0OU13Z0JjZkFxWjFhNng= |
3、base64:
1 | RXhaGqe7ZcQBmqriiyKFJin27fbZJSdxNwhAVMp74oQa4Uk6EujNZdLsoaZq4tLP7wuy88bbJXeLbg7gqGddNmytk5KTFvY7NjQGL3zqkCpB3yfQ1SRF49MwgBcfAqZ1a6x |
4、 base58:
1 | G53XC4LIK5DWQ53UIFSGCUTCJFCGM4DSM5UXOYTILBUXU6TXJ5SUUT2DONHTQZ3GJNCFSUDINRXE6MTEINUXOQLVLI4VU=== |
5、 base32:
1 | 7wqqhWGhwtAdaRbIDfprgiwbhXizzwOeJOCsO8gfKDYPhlnO2dCiwAuZ9Z |
6、base62:
1 | SICTF{fe853b49-8730-462e-86f5-fc8e9789f077} |
flag:
SICTF{fe853b49-8730-462e-86f5-fc8e9789f077}
Radio
题目描述:
1 | 树木新开发了一个加密系统,这个系统会把他的秘密加密很多次然后发送给不同的用户,你能找到其中的漏洞吗? |
题目:
1 | from Crypto.Util.number import * |
经典的广播攻击,思路就是使用中国剩余定理得到$\quad mod \; (n1n2n3)\quad$下的$\quad m^{17}\quad$,再开17次方根即可。
exp.py:
1 | from sympy.ntheory.modular import crt |
flag:
SICTF{fdc0afb5-1c81-46b9-a28a-241f5f64419d}
MingTianPao
题目描述:
1 | 这个题目名充分表现了作者由于学CTF导致吃不上饭,明天就打算跑路的心里想法。 |
题目:
1 | import binascii |
很明确的一个Many-Time-Pad,也对应了题目名字MTP,预期来说应该是上一个知名MTP脚本求解。
但是其实完全不需要,因为题目给了这样一个提示:
1 | # message is a Classic English Story |
我们又有flag的前六个字符:SICTF{
那么拿去异或一下就有:
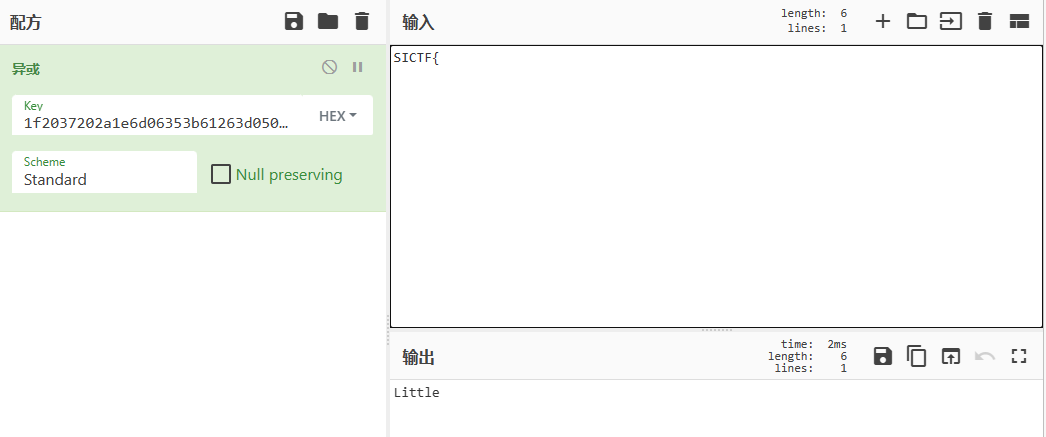
合理猜测这是一个Little开头的英语故事,那么由于异或的可逆性,直接把密文搬上明文的位置,来试几个:
Little Prince(小王子):
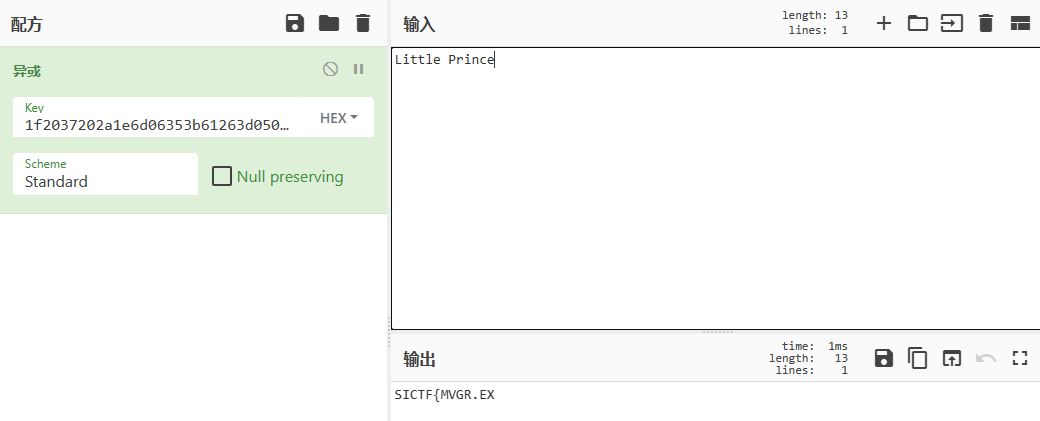
不太对,换一个,Little Red Riding Hood:
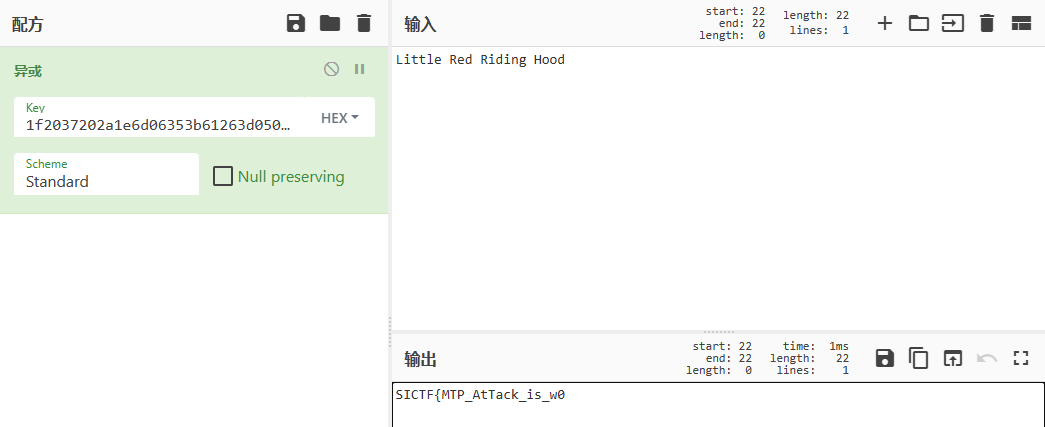
这就成了,又可以看出flag串后面应该是wonderful的变形,那么再把flag串搬上来逐个尝试即可:(因为可以变的其实就大小写、以及形近数字,一个字符一个字符增加,试几次就出来了):
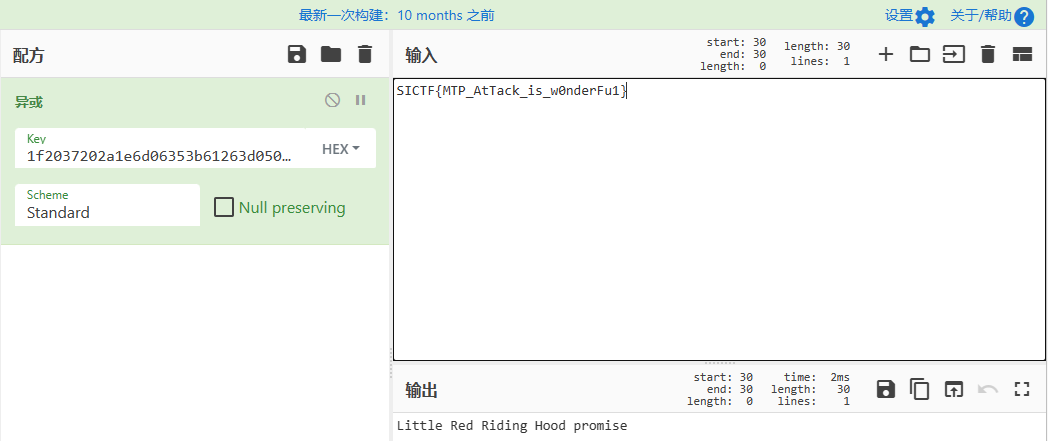
flag:
SICTF{MTP_AtTack_is_w0nderFu1}
Easy_CopperSmith
题目描述:
1 | 你知道CopperSmith吗? |
题目:
1 | from Crypto.Util.number import * |
直白的p高位泄漏,直接解密即可。
exp.ipynb:
1 | from Crypto.Util.number import * |
flag:
SICTF{3f9366ed-b8e4-412f-bbd0-62616a24115c}
签到题来咯!
题目描述:
1 | 签到题来咯! |
题目:
1 | from secret import flag |
经典的明文相关消息攻击,略做了一点变种。思路如下,列出两个多项式:
又因为明文m显然是两个模多项式的根,因此两个模多项式有公因子:
因此构造出模n环下的两个多项式,并求公因式即可。至于e是多少,仅需要在指定范围内爆破一下就可以。
exp.ipynb:
1 | from gmpy2 import * |
flag:
SICTF{hhh!!franklin_reiter_is_easy}
small_e
题目描述:
1 | 这个低加密指数攻击为什么打不出来哇?是不是题有问题捏?差评! |
题目:
1 | import libnum |
已知明文高位攻击,直接上脚本。
exp.ipynb:
1 | from Crypto.Util.number import * |
flag:
SICTF{2ca8e589-4a31-4909-80f0-9ecfc8f8cb37}
easy_math
题目描述:
1 | 其实数学很简单辣! |
题目:
1 | from secret import flag |
注意到hint1、hint2的生成过程:
而p前的系数a1、a2很小,因此可以先打印出所有13比特的素数存在一张表内,作为a1、a2的所有可能取值,然后如下操作:
与n求gcd即可得到q,之后进行RSA解密即可。
exp.py:
1 | from Crypto.Util.number import * |
flag:
SICTF{452aebb6-9c16-441a-ac42-fc608bf6063f}
总结
越熟练手速就会越快,继续努力!