比赛记录
[Week 1] What’s CBC?
题目描述:
1 | 经典的加密预处理? |
题目:
1 | from Crypto.Util.number import * |
题目比较简单,就不梳理流程了,主要漏洞在于encrypt函数中:
1 | result += ((i^key)).to_bytes(1,'big') |
可以看到,key只用了最低的一个字节来进行加密,因此有两种思路:
- 爆破256种可能的key,均进行解密,在解密出来的文本中,有0xGame的flag头即为正确解密
- 用已知的0xGame这个flag头直接确定key,再进行解密
不管用哪个思路,最终发现key的最低字节是 b’\x8f’
exp:
1 | from Crypto.Util.number import * |
[Week 1] 密码,觅码,先有*再密
题目描述:
1 | 在开始挑战BOSS前,先来通关新手村吧 |
hint:
1 | Hint 1: Test your python |
题目:
1 | from secret import flag #从中导入秘密的flag,这是我们要破解的信息 |
可以看到flag被分为四份,进行不同的编码,那么首先要对应解码:
1 | b'0xGame{ \xe6\x81\xad\xe5\x96\x9c\xe4\xbd\xa0,\xe5\xb7\xb2\xe7\xbb\x8f\xe7' |
解出来后,发现解密内容除了flag头尾,剩下的仍然是字节流,猜测可能是汉字编码,解码即可
exp:
1 | from Crypto.Util.number import * |
[Week 1] Take my bag!
题目描述:
1 | 我包呢? |
题目:
1 | from Crypto.Util.number import * |
一个背包加密,需要注意到的是这里的 pow(3, i) 是一个超递增序列,因此有两种方法:
- 直接当作普通背包加密,用格基规约做
- 如果flag长度较短,那么很可能前面的背包加密根本没有取模,可以直接当作超递增序列解密
无论哪个方法都不麻烦,当然因为是新生赛所以推荐先学会第二种方法
exp:
1 | from Crypto.Util.number import * |
[Week 1] BabyRSA
题目描述:
1 | 经典的数学,经典的算法 |
题目:
1 | from Crypto.Util.number import * |
多素数的RSA,factordb分解后直接解密即可,最后还需乘上mask的逆元
exp:
1 | from Crypto.Util.number import * |
[Week 1] 猜谜
题目描述:
1 | 什么情况,密钥不见了?(flag格式: 0xGame{}) |
题目:
1 | from secret import flag,key |
加密流程如下:
- flag 是一个字节流,记其长度为 l
- 将 flag[i] + i 与 key[i%7] 异或,并转为一个字节后,得到 encrypt(flag)
- 将 encrypt(flag) 进行 enc 加密
其中,enc加密过程为:
- 将 encrypt(flag) 的每个字节转化为二进制,并补齐 8 位
- 把每个字节的二进制再拼接在一起,得到一个01串
- 将01串每三位转化为十进制数,作为当前需添加的密文字符在 code 中的下标
- 添加完所有密文后,填充上对应补充字节,作为密文给出
那么解密流程就是:先恢复 enc,再恢复 encrypt
enc的恢复是容易的,简单逆向回去就行,当然需要注意一下解填充:
1 | code = 'AP3IXYxn4DmwqOlT0Q/JbKFecN8isvE6gWrto+yf7M5d2pjBuk1Hh9aCRZGUVzLS' |
然后就是恢复encrypt,注意到我们拥有flag头0xGame{,刚好七个,因此可以直接恢复密钥,然后对应解密
exp:
1 | from Crypto.Util.number import * |
[Week 1] Vigenere
题目描述:
1 | 密文:0dGmqk{79ap4i0522g0a67m6i196he52357q60f} 古老而神秘的加密方式? |
没有附件,那么结合题目内容就知道用的是Vigenere加密,上cyberchef,直接用flag头就能看出密钥是game:
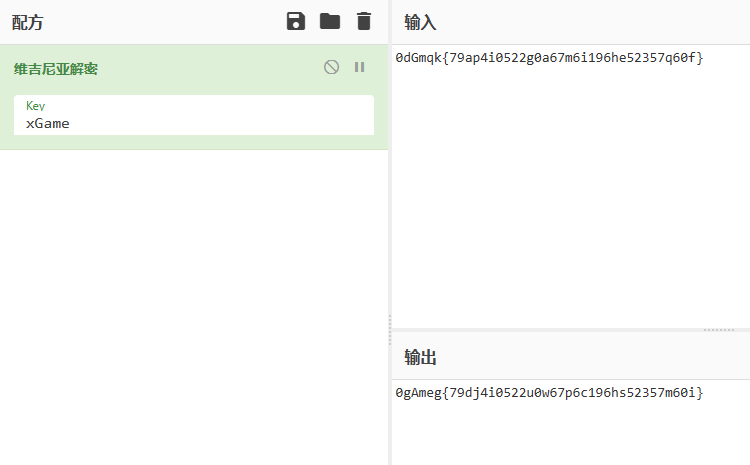
那么用game解密就好:
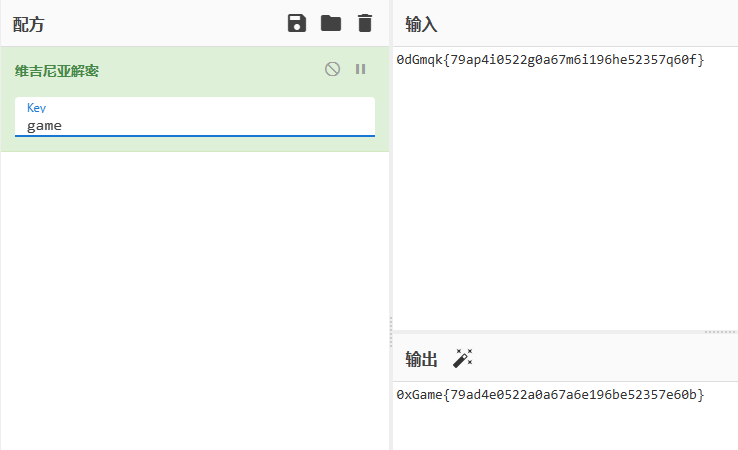
flag:
0xGame{79ad4e0522a0a67a6e196be52357e60b}